Give and Ye Shall Receive! The Copyright Implications of BitTorrent
Bob Rietjens*
|
Table of Contents: 1. INTRODUCTION 2. HOW DOES BITTORRENT WORK? 3. REPRODUCTION, MAKING AVAILABLE AND DISTRIBUTING 3.1 Reproduction 3.2 Distributing 3.3 Communicating and Making Available to the Public - Intermezzo 3.4 Making Available to the Public – The Narrow Test 3.5 Communication to the Public– The Broader Test 4. EXCEPTIONS AND LIMITATIONS 4.1 Private Copying Exception 4.2 Temporary Copies 4.3 Mere Conduit 5. CONCLUSION 6. BIBLIOGRAPHY |
|
Cite as: B Rietjens, "Give and Ye Shall Receive! The Copyright Implications
of BitTorrent", (2005) 2:3 SCRIPT-ed 327 @:
http://www.law.ed.ac.uk/ahrc/script-ed/vol2-3/torrent.asp
|
|
© Bob Rietjens 2005. This work is licensed with the Creative Commons
BY-ND Netherlands Licence.
|
1. INTRODUCTION
BitTorrent's peer-to-peer (P2P) "file-swarming" software currently uses more than a third of the Internet's bandwidth.1 BitTorrent primarily owes its popularity to its fast download rates. It takes hours to download a ripped version of the latest episode of Desperate Housewives off Kazaa, but with BitTorrent it takes minutes.
In some EU countries it is legal to download copyright protected content using P2P software under private copy exceptions.2 As long as P2P users don’t upload, they are not liable for copyright infringement. But with BitTorrent, it is not possible to just download, as the idea behind BitTorrent is that users all download small pieces of the file, and then start uploading these small pieces to each other.
This essay analyses whether using BitTorrent amounts to infringement of copyrights or related rights. It will proceed according to the following plan. Chapter 2 outlines how BitTorrent works. Chapter 3 then outlines to what extent the use of BitTorrent entails making reproductions, distributing works, making works available, and communicating works to the public. Chapter 4 then assesses whether copyright exceptions can benefit the users of BitTorrent. Chapter 5 concludes with some final remarks.
Rather than focussing on one single jurisdiction, this essay looks at the situation in the EU in general. However, reference shall be made to several jurisdictions in the EU for illustration purposes. Although the conclusions drawn in this essay give a comprehensive general overview of the legal implications regarding BitTorrent, two reservations must be made: (i) reference is made to several EU directives3 and international intellectual property treaties.4 These directives and treaties depend on implementation in national laws. Although implementation has a harmonising effect, differences remain in how countries implement directives and treaties; and (ii) in some areas no harmonisation has taken place at all. It should also be noted that there are P2P programs available that have similar features as BitTorrent, such as Exeem and eDonkey. This essay only reflects on BitTorrent, but the arguments in this essay may apply mutatis mutandis to other P2P programs with similar technical properties.
2. HOW DOES BITTORRENT WORK?
BitTorrent is a P2P file distribution tool written by programmer Bram Cohen. How does it work? Let’s say that you want to download the latest episode of Desperate Housewives via BitTorrent. First, you have to find a static file with a .torrent extension for your desired episode. These files are normally published on websites or distributed by email, and contain information (metadata) about the file you are looking for: its length, name, hashing information, and the URL of the tracker (discussed below). You will then have to download this .torrent file to your computer.
Next, you have to open the .torrent file (that you downloaded) on your computer in a BitTorrent client software program. The .torrent file then tells the client software the IP address of the tracker, which then makes a connection to the tracker. A tracker is not directly involved in uploading or downloading files. Instead, the tracker tells your client software the location of all those who have downloaded the same .torrent file and are in the process of downloading the file (the peers). The client software then uses this information to start connecting to these peers; this is called your peer set. A swarm is the total number of people simultaneously downloading the same .torrent file.
Next, the BitTorrent client software starts downloading small parts (typically 256kB each) of the Desperate Housewives file you requested from different peers in your peer set in random order. Each time you complete downloading one of these parts, your BitTorrent client software informs the peer set. Your BitTorrent client software then, upon request of other peers in your peer set, uploads these small parts to them. In other words, you send parts that you have finished downloading as you request finished parts from others, and vice versa.
Two kinds of peers can be distinguished. Those who are in the process of downloading the file are called leechers. It is important to note that leechers cannot disable this uploading. As long as somebody leeches, he has to upload parts of the file to other peers. Those peers who have already completed downloading the complete file are called seeds. Seeds are used as sources of parts of the file until they close their BitTorrent client software.
Traditional P2P programs such as Napster, Kazaa and Limewire have a bottleneck, because uploading and downloading does not happen at equal speed. If you, therefore, want to download a specific file with traditional P2P programs, your download rate depends on the upload speed of the person you are downloading from (figure 1). With BitTorrent, you are downloading tiny parts from a large number of people, and as many hands make light work, BitTorrent reaches much faster downloading rates (figure 2). With BitTorrent, the more popular a file, the more uploaders there are (because more people are downloading), and the faster downloading gets. This greatly contrasts with traditional P2P programs where the more popular a file is, the slower it downloads.5
Figure 1: Traditional P2P
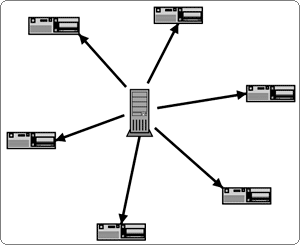
Figure 2: BitTorrent
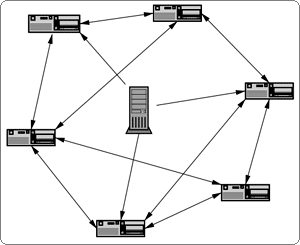
Source: www.bittorrent.com
3. REPRODUCTION, MAKING AVAILABLE AND DISTRIBUTING
This chapter assesses whether the use of BitTorrent entails acts of reproduction (paragraph 3.1), distribution (paragraph 3.2), making available (paragraph 3.4) or communication to the public (paragraph 3.5). It primarily focuses on uploading activities. Just because an action falls within the domain of reproduction, distribution, making available or communicating to the public, this does not necessarily lead to infringement; these rights are subject to important limitations and exceptions. Chapter 4 deals with these limitations and exceptions.
3.1 Reproduction
The right of reproduction is not included in the World Copyright Treaty (WCT). However, this treaty does mention that parties shall comply with the Berne Convention. The Berne convention requires member states to grant the exclusive right of reproduction to authors.6 The Agreed Statement to the WCT mentions that the reproduction right as included in the Berne Convention applies in the digital environment, in particular to the use and storage of works in digital form.7 The WIPO Performances and Phonograms Treaty (WPPT) also includes the reproduction right.8
The Infosoc Directive gives more guidance as to the scope of the reproduction right, stipulating: “Member States shall provide for the exclusive right to authorise or prohibit direct or indirect, temporary or permanent reproduction by any means and in any form, in whole or in part: (a) for authors, of their works; (b) for performers, of fixations of their performances; (c) for phonogram producers, of their phonograms; (d) for the producers … of films…; (e) for broadcasting organisations, of … broadcasts.”9
To what extent is this right of reproduction infringed by the use of BitTorrent? To understand BitTorrent, one first has to understand how Internet works. Internet operations require continuous copying.10 Suppose that you want to download a file from a server. This file is actually no more than a string of ones and zeros stored on a storage device (as is all data on a computer). What actually happens if you download this file, is that your computer sends an instruction to the server to send you a copy of the file (not considering mirror sites and caching). A copy of the file is then made and split up into packets that are subsequently sent out via the Internet. Different computers (intermediaries) then copy and retransmit the packets until they reach your computer. Before your hard disk stores the final copy, several temporary copies are made. Downloading and uploading a file thus entails multiple acts of copying by the uploader, the intermediaries and the downloader.11
As demonstrated in Chapter 2, the use of BitTorrent entails both downloading from, and uploading to, other peers in the peer set. Therefore, the BitTorrent user engages in copying parts of the file in the process of uploading and downloading, even if the end result is that every downloader ends up with only one permanent copy. The relevant question is whether the temporary copies and the final copy made in the process of downloading and uploading are reproductions as meant in the Infosoc Directive. There can be little doubt that the final copy is a reproduction in the sense of article 2 Infosoc Directive because it is a perfect permanent copy of the original file. More interesting is whether the temporary copies made in the process of downloading and uploading are reproductions. There are two distinct legal issues that need to be addressed in this respect: (i) Does the right of reproduction cover temporary copies? (ii) Is the fact that only copies of parts of the file are reproduced relevant? These two issues will now be addressed.
In a digital world copies are often fleeting and there have been questions whether these temporary copies are really reproductions that should be granted exclusive rights over.12 No agreement was reached in this respect in the WCT,13 and the WPPT is also silent on this matter. The Infosoc Directive, however, explicitly provides that the right of reproduction includes temporary and permanent reproductions. Thus, the reproduction right also covers ephemeral copies.14 This brings BitTorrent downloading and uploading in the domain of the reproduction right.
Parts of the file that you need to complete your copy of the file are downloaded from other peers in your peer set in random order. The BitTorrent client subsequently reassembles these downloaded parts into a complete file. Although downloading eventually results in one complete copy of the file, downloading entails copying small parts of the ultimately downloaded file. The same goes for uploading, as only small parts of a file are uploaded (and thus copied). Unless you are a seed, you will not necessarily distribute all the parts of a file that are needed to reassemble a perfect copy.
Copyright laws often struggle with the question whether a non-perfect or a partial copy amounts to copyright infringement. The approach adopted in the UK, for example, that there is only reproduction in case a substantial part has been copied.15 This criterion raises questions on whether there can be infringement by the reproduction of a small part of a digital file.16 For example, the court in Electronic Techniques (Anglia) Ltd v Critchley Components clearly struggled with this question.17 This should be a concern of the past, as the Infosoc Directive clearly states that the reproduction right embodies reproductions “in whole or in part”.18
The above demonstrates that it is not only the permanent copy of the complete file that is relevant in relation to the reproduction right. In the process of downloading and uploading, temporary copies are made that are covered by the reproduction right granted to rights holders (subject to the copyright exclusions dealt with in Chapter 4). The next paragraph examines whether the use of BitTorrent entails acts of distribution.
3.2 Distributing
The distribution right mentioned in article 6(1) of the WCT relates to distribution of “… originals and copies of … works … ” The Agreed Statement makes clear that this article exclusively refers to fixed copies “that can be put into circulation as tangible objects.”(emphasis added). Thus, the reproduction right only has significance for physical copies.19 The distribution right as included in the Infosoc Directive is not relevant for the same reason. Although article 4 Infosoc Directive does not explicitly exclude the distribution of digital copies, the preamble makes clear that the distribution right relates to “distribution of the work in a tangible form.”20 Therefore, the distribution right as included in the Infosoc Directive has no bearing on the use of BitTorrent, and shall not be reflected on further. The use of BitTorrent only concerns copies in intangible form.
3.3 Communicating and Making Available to the Public - Intermezzo
The right of communication and making available to the public is complex, and therefore requires some explanation before application to BitTorrent. A distinction should be made between protection of literary and artistic works on the one hand, and protection of performances, phonograms, films and broadcasts on the other hand.
The Berne Convention grants authors fragmented rights of communication to the public. These rights were sufficient to deal with 20th century technologies.21 However, problems arose after the advent of the Internet. The first problem was that the rights of communication to the public in the Berne Convention are rather fragmented. 22 The establishment of the WCT reached a breakthrough by granting authors a more overarching right of communication to the public. This WCT right only applies to the extent that the acts of communication are not covered by the Berne Convention.23
The second problem with the application of the Berne Convention to the Internet was whether making works available through the Internet could be considered a “communication to the public”, as the notion of public on the Internet is dismembered from three conceptual points: space, time and object.24 In other words, is there a “public” if different versions of a work can be reached by different people at different times? The solution reached was that the concluding words of Article 8 WCT mention that the right of communication to the public includes “… the making available to the public of … works in such a way that members of the public may access these works from a place and at a time individually chosen by them.” This makes clear that interactive, on-demand systems – publishing works on the Internet – are also covered by the right of communication to the public.25 The important question thus is whether a work is able to reach anybody.26 The Infosoc Directive adopted a right of communication (including the right of making available) in similar words for copyright works.27
How then does this relate to the protection of performances, phonograms, films and broadcasts? Simply put, there is no broader right of communication for these subject matters. The WPPT28 and the Infosoc Directive29 merely require members to grant a right of making available. Thus, where copyright holders have the exclusive rights to authorise any kind of communication to the public, performers, record and film producers/directors and broadcasters are only given control over the broadcast of their works through on-demand services.30 Under the WPPT performers and producers of phonograms should, however, be granted a remuneration right for the use of phonograms published for any communication to the public.31 How does this relate to BitTorrent? Paragraph 3.4 ascertains the situation as to the (more narrow) right of making available to the public. Paragraph 3.5 then assesses whether the use of BitTorrent entails acts of communication to the public.
3.4 Making Available to the Public – The Narrow Test
The making available right was included to adapt copyright to the technologies of the 21st century. But the wording seems to be outdated if one looks at BitTorrent. A distinction should be made between seeds and leechers. The role of a seed is very important with BitTorrent. There has to be at least one seed connected for a swarm to complete downloading all the parts of a file.32 The making available right applies to seeds. As long as a seed stays online, the public may access these works from a place and at a time individually chosen by them by downloading the .torrent file and opening this file in the BitTorrent client software. Leechers send most of the parts of the files. But indirectly, all parts of the file originate from one or a limited number of seeds. A seed is therefore engaged in the act of making available to the public.
But most of the file sharing takes place between leechers. And the majority of the peers in a swarm are leechers and not seeds. Are leechers involved in acts of making protected works available to the public? The making available right seems to be tailored to the needs of point to point or point to multipoint communication, such as situations where one person makes a work available for download on a website. It has problems with adapting to the swarming technique utilised by BitTorrent. The timeframe within which leechers make specific files available for upload by leechers is very limited. Again, it takes hours to download a ripped version a television show off Kazaa, but with BitTorrent it only takes minutes. Only within this limited timeframe, is the file made available for download. It seems questionable whether such a small amount of time would allow downloading “at a time individually chosen by” the downloader. The downloader chooses the specific time of download, but as the timeframe is limited, there is hardly an option. Furthermore, the choice of the public in the WCT, WPPT and the Infosoc Directive is more directed at the time at which downloading is initiated than at the time when a particular part of a file is downloaded from a particular user. After the actions that initiated downloading, there hardly seems to be any choice for the downloader, as the BitTorrent client software makes all the choices for him.
3.5 Communication to the Public– The Broader Test
Thus, with regard to the file sharing that takes place between leechers, we have to fall back on the general right of communication to the public. It is, however, questionable whether the activities of leechers are to be considered as acts of communication to the public.
The Infosoc Directive and WIPO treaties do not define the word “communication”. The WCT gives little interpretative guidance on the notion of the communication right.33 Communication normally seems to refer to acts such as: performing, showing, playing, broadcasting, etc.34 The inclusion of the word “any”, and the coverage over communication by wire and wireless communications, reflect the intention to provide for a technology-neutral right.35 The explanatory notes to the basic proposal of the WCT make clear that it includes any making available of a work other than by distributing (tangible) copies.36 It includes transmission and distribution of copyright works other than in physical form, i.e. it covers communication to the public of copyright works via online means of distribution, such as the Internet or by broadcasting.37 The inclusion of the word “any” also seems to indicate that it is not relevant at whose imputes the transmission occurs: the communication right covers both “pull” technologies (when the recipient initiates the broadcast), and “push” technologies (when the sender initiates the broadcast). It thus seems to include all kinds of transmission, including uploading files between leechers.
Is a peer set or a swarm “public”? The Infosoc Directive, the WPPT and the WCT do not give any definition of the word “public”. Much will depend on how national laws define this word.38 Most jurisdictions exclude from the definition of public those uses that take place within the confines of a circle of friends and family.39 In general, it has been said that point-to-point communication does not qualify as public if the sender initiates the communication.40 For example, sending an email to one particular person does not constitute making available to the public, even if this person is a member of the public rather then someone from your family circle.41 But with BitTorrent it is not one message that is sent to one member of the public. Parts of a work are send all over the world to people that are unknown to the leecher. Furthermore, the aim of these treaties and laws is to give the author the exclusive right to exploit his work by way of communication to the public. Thus, the interpretation of “public” should not be such as to adversely affect the exploitation right of the author.42 The word “public” thus includes peers in a particular peer set or swarm.
Use of BitTorrent, therefore, seems
to entail communication to the public, but there is one more wrinkle
that has to be dealt with. In contrast to the reproduction right,
where it is explicitly mentioned that the right covers reproduction
of the work “in whole or in part”,43
article 8 of the WCT, articles 10 and 14 of the WPPT, and article 3
of the Infosoc Directive merely refer to “the work”. Does
the right of communication therefore extent to the transmission of
small parts of a work? This can be argued both ways. On the one hand
a contrario reasoning leads to the conclusion that uploading parts
of a work would not amount to making available. If the WCT aimed to
include communication of parts of the work, it would have adopted the
same language it adopted in regards of the reproduction right, i.e.
communication in whole or in part). On the other hand, one has to
take into account that the ratio behind the right of communication to
the public is that rights holders are able to control the
dissemination of their work through all possible media, and
specifically information networks and digital media.”44
Furthermore, it might be that each communication only takes place in
regards of small packets. The fact of the matter is that all
communication on the Internet occurs in small packets. It could,
therefore, be argued that one would have to look at the end result.
In the end, every leechers has send a considerable amount of these
small packets that in total would at least amount to a substantial
part in a qualitative sense.
4. EXCEPTIONS AND LIMITATIONS
Chapter 3 concluded that BitTorrent use results in acts covered by the right of reproduction, but that it is arguable whether BitTorrent use entails acts of communication to the public. The right of reproduction and the right of communicating/making available to the public, however, are not absolute, and their scope is limited by various exceptions and limitations. These exceptions and limitation function to balance the economic interests of copyright holders and the interests of users.45 This chapter assesses whether BitTorrent users can benefit from any of these exceptions. This Chapter reflects on the following three exceptions: the private copying exception (paragraph 4.1), the temporary copy exception (paragraph 4.2) and the mere conduit exception (paragraph 4.3). The first two exceptions pertain to acts of reproduction. The mere conduit exception has a more horizontal approach and applies to all kinds of liabilities arising from transmitting information.
Because most exceptions are optional the Infosoc Directive establishes a low degree of harmonisation with regard to exceptions.46 This leaves the member states with considerable freedom to provide for various exceptions.47 For example, The Netherlands has implemented the private copying exception48, while the UK as not.49
However, the temporary copies exception included in article 5(1) of the Infosoc Directive is, however, mandatory. The “mere conduit” exception included in article 12 of the E-commerce directive is also mandatory.
4.1 Private Copying Exception
One exception that could benefit users of BitTorrent in (parts of) the EU is the private copying exception. This exception is also included in article 5(2)(b) of the Infosoc Directive, though it should be noted that some argue that the private use exception should not apply in a digital environment in the future. According to Hugenholtz, for example, the private use exception should be phased out if technological measures can be applied realistically and legally in the market place.50 However, as these technological measures are not yet available, private copying exceptions apply in full to the digital environment.
The question is whether users of BitTorrent can benefit from this exception (provided that the private copying exception is implemented into the copyright laws of a particular member state). Prior to the implementation of the Infosoc Directive, Dutch literature generally assumed that downloading (copying) works from P2P networks was covered by the private copying exception existing,51 and Dutch jurisprudence supported this view.52 The implementation of the Infosoc Directive does not seem to have altered the scope of the private copying exception under Dutch law. Article 5(2)(b) Infosoc Directive reads as follows: “Member States may provide for exceptions or limitations to the reproduction right … in the following cases: … (b) in respect of reproductions on any medium made by a natural person for private use and for ends that are neither directly nor indirectly commercial, on condition that the rightholders receive fair compensation which takes account of the application or non-application of technological measures referred to in Article 6 to the work or subject-matter concerned.” Recent jurisprudence in France also recognises that the private copying exception as included in the Infosoc Directive covers downloading.53
But with BitTorrent there is more to it. As mentioned, a leecher also has to upload parts of the file to other peers, and as mentioned in Chapter 3 this entails acts of reproduction. The question then is, are these acts of reproduction also covered by the private copying exception? Article 5(2)(b) Infosoc Directive requires that the copy is made by “… a natural person for private use … .”The question then of course is: does the person copying have to be the user? The wording of article 5(2)(b), and the recitals of the preamble of the Infosoc Directive pertaining to private copying, does not give an answer to this question. The Dutch legislature, for example, has firmly taken the position that the person copying and the user should be one and the same person.54 The connotation of the word “private” in this respect is that the copy: “... belongs to, or is the property of a particular individual…”55 If this interpretation is correct, BitTorrent users cannot enjoy protection under the private copying exception, as copies made in the process of uploading are not made for the private use by the uploader.
A somewhat broader interpretation of the word “private” connotes use that is “not open to the public”.56 In this sense private use (listening, playing, watching, etc.) refers to use in a private environment, regardless of who is using it. In this sense, the private copying exception not only covers downloading activities within the BitTorrent network, but arguably also uploading activities, as peers will (presumptively) use the copy made in a private environment. There is a strong historical argument in favour of this interpretation. The private use exception has its roots in Germany where it was introduced to protect users of copying equipment against invasions of their private sphere. 57 In this sense “private” refers to private environment rather than a particular individual. But even if this interpretation is adopted, the onus of proof of private reasons by everybody that has received parts of the files lies with the uploader. This seems impossible to prove.
Thus, reproductions made in the process of downloading (including the final copy) are covered by the private copy exception. But this exception does not cover uploading activities, and as uploading cannot be disabled, the use of BitTorrent is not covered by the private copy exception. Therefore, it will be of interest to see whether the temporary copy exception can benefit the BitTorrent users in their downloading (and thus uploading) activities.
4.2 Temporary Copies
Paragraph 4.1 showed that the private use exception does not cover copies made in the process of uploading (parts of) a file to other peers. This paragraph will therefore assess whether these copies are covered by the exception pertaining to the reproduction for temporary copying. This exception is complex and is subject to requirements that limit its scope.58 A temporary reproduction does not amount to copyright infringement in cases where the reproductions: (i) are transient or incidental; (ii) are an integral and essential part of a technological process; (iii) have the sole purpose to enable a transmission in a network between third parties by an intermediary or a lawful use of a work; and (iv) have no independent economic significance.59
The first two steps and the last step do not cause great difficulties in lieu of BitTorrent use. In the process of uploading parts of a file, uploaders only make temporary copies.60 In this sense, the copies made by uploaders are transient. The second step is also met, as temporary copies made are an integral and essential part of a technological process, i.e. uploading files. The last step does not bar the application of the temporary copy exception either, as the copy made for the purpose of uploading has no independent economic significance. As mentioned, with BitTorrent a large file gets split up into small parts. And it is these small parts that are distributed by each peer. As these small parts cannot be used on their own, copying these small parts have no independent economic significance.
The third step is more difficult. The copy must be made for the sole purpose to enable: (i) a transmission in a network between third parties by an intermediary; or (ii) a lawful use of a work. Of course one can argue that every peer is an intermediary between the seed and the other peers. But the word “sole” invalidates this interpretation, as every downloader makes a permanent copy of a file for himself before he sends it to other peers.
Then what about the second option: is the temporary copy made in the process of uploading made to enable the lawful use of a work? First, this depends on what is considered use, in the context of BitTorrent. In this author’s view, sending a copy of a small part of a file can in itself hardly be described as using a work. Thus, the use in “enabling lawful use” probably refers to the use made by the peer that the file is sent to.
Secondly, one then has to assess whether this use is lawful. This depends on how one defines a lawful user. The Database Directive and the Software Directive both also utilise a vague notion of a “lawful user”.61 If one defines a lawful user as somebody who has a contractual licence (a limited interpretation), the temporary copy exception cannot apply to the use of BitTorrent. If lawful also includes use in conformity with a copyright exception, the following picture emerges.62 If this peer can claim lawful use under a copyright exception of his own law, sending that file to him enables lawful use. But this requires every BitTorrent user to check in which jurisdiction the peers in his peer set are located and to what extent the use of downloaded versions of protected works is allowed in that jurisdiction. This is not an option, thus, the temporary copy exception cannot benefit those using BitTorrent.
4.3 Mere Conduit
The E-Commerce Directive provides that a provider acting as a “mere conduit” cannot be held liable for the information transmitted.63 Can those using BitTorrent benefit from this exclusion? With BitTorrent, downloaders upload files to other peers. In this sense, downloaders hardly seem to qualify as intermediaries. But if one looks at the whole peer set, another picture emerges. In this picture, it is the seed (or several) seeds that spread all the parts of a file. The other peers then subsequently distribute these parts amongst each other. In this context, a downloader seems to take on an intermediary role between a seed and the other peers.
The “mere conduit” stipulation, however, contains strict limitations on its scope that prevent from providing BitTorrent users any shelter against infringement claims. First, it applies only to service providers who provide an “information society service”.64 A BitTorrent user does not meet this test, as it does not provide a service that is normally provided for remuneration. Second, the data may no longer be stored than necessary for a transmission”.65 BitTorrent users, however, maintain a copy of the file distributed for themselves. Thirdly, the provider may not select the receiver of the transmission.66 With BitTorrent, peers send messages to other peers if they have a file available for download. This could be construed as selecting the receivers of a file.
5. CONCLUSION
The advent of BitTorrent has not gone unnoticed by the copyright industry. For example, the music industry claims that it recently closed down 50 file-sharing hubs in Australia.67 But the future seems to hold P2P software that utilises BitTorrent technology, without the need for trackers, as nodes in the P2P program takes their role.68 These developments will urge the music industry to attack the users of these programs rather than those who facilitate it as trackers.
As demonstrated the use of BitTorrent clearly entails acts of reproduction. And as the use of BitTorrent requires that parts of files are uploaded to other peers, a function that cannot be disabled, BitTorrent users cannot benefit from the private copying exception and the temporary copy exception. Because also the mere conduit exception does not apply, the use of BitTorrent clearly infringes copyrights and related rights of rights holders.
In a recent essay, Professor Ginsburg stated that “[D]espite the aim of the WIPO Treaties to assure effective and uniform protection of the rights of authors, technology may continue to outstrip the ingenuity of the drafters…”69 In the light of this comment it is interesting to notice the difficulties in applying the right of making available and/or communicating to the public to BitTorrent use.
6. BIBLIOGRAPHY
Books
Alberdingk Thijm 2004
Chr.A.
Alberdingk Thijm, Het Nieuwe Informatierecht: Nieuwe Regels
voor het Internet, Den Haag: Academic Service, 2004.
Burrell & Coleman
R. Burrell & A. Coleman,
Copyright Exceptions: The Digital Impact, Cambridge:
Cambridge University Press, 2005.
Ficsor 2002
M. Ficsor, The law of copyright
and the Internet: the 1996 WIPO treaties, their interpretation and
implementation, Oxford: Oxford University Press, 2002.
Hugenholtz 1996
P.B. Hugenholtz, The future of
copyright in a digital environment: proceedings of the Royal
Academy Colloquium organized by the Royal Netherlands Academy of
Sciences (KNAW) and the Institute for Information Law,
(Amsterdam, 6-7 July 1995), The Hague: Kluwer Law International,
1996.
Lodder & Kaspersen 2002
A.R. Lodder & H.W.K. Kaspersen
(eds.), eDirectives: guide to European Union Law on E-Commerce,
The Hague, Kluwer Law International, 2002.
Reed 2004
C. Reed, Internet Law,
Cambridge: Cambridge University Press, 2004.
Reinbothe 2002
J. Reinbothe & S. Lewinski,
The WIPO treaties 1996: the WIPO Copyright Treaty and the WIPO
Performances and Phonograms Treaty: commentary and legal analysis,
London: Butterworths, 2002.
Spoor 1996
J. Spoor, ‘The Copyright
Approach to copying on the Internet: (over) Stretching the
Reproduction Right’, Hugenholtz 1996, 67-80.
Stokes 2002
S. Stokes, Digital Copyright:
Law and Practice, London: Butterworths, 2002.
(Online) journals and other (online)publications
Arkenbout 1997
E.J. Arkenbout, ‘Nieuwe
Verdragen over Auteursrecht en Naburige Rechten’,
Informatierecht/AMI 1997.
Arkenbout 2001
E.J. Arkenbout, ‘Richtlijn
Auteursrecht en Naburige Rechten in de Informatiemaatschappij:
Naar een Europees Auteursrecht, Computerrecht 2001-3.
Bannink 2001
H. Bannink,
‘Noot bij KaZaA/Buma-Stemra, Gerechtshof Amsterdam, 28 maart
2002, rolnr. 1370/01’, JAVI 2002(1), 28-29.
Benkler 2004
Y. Benkler, ‘Sharing Nicely:
On shareable goods and the emergence of sharing as a modality of
economic production’, 114 Yale L. J. 273 (2004).
Cohen 2003
B. Cohen, ‘Incentives Build
Robustness in BitTorrent’,
(http://www.bittorrent.com/bittorrentecon.pdf), (28 March 2005).
Copyinger
2005
––, ‘Copinger
and Skone James on Copyright’, (http://www.westlaw.com)(5
April 2005).
Fabiani 1997
M. Fabiani, ‘The Geneva
Diplomatic Conference on Copyright and the Rights of Performers
and Phonogram Producers’, Ent. L.R. 1997, 8(3), 98-102).
Geiger 2005
C Geiger, ‘Right to Copy v.
Three-Step Test The Future of the Private Copy Exception in the
Digital Environment’, CRi 1/2005.
Ginsburg 2004
J.C. Ginsburg, ‘The (New?)
Right of Making Available to the Public’,
(http://lsr.nellco.org/columbia/pllt/papers/0478)(7 April 2005).
Goldstein 2001
P. Goldstein, International
copyright: principles, law, and practice, Oxford: New York,
Oxford University Press, 2001.
Hart 2002
M.
Hart, ‘The Copyright in the Information Society Directive:
An Overview’, E.I.P.R. 2002, 24(2), 58-64).
Hugenholtz 2001
P.B. Hugenholtz, ‘Brussels
Broddelwerk: Recht en Krom in de Auteursrechtrichtlijn’, AMI
2001-1.
Hugenholtz 2003
P.B. Hugenholtz and others, ‘The
Future of Levies in a Digital Environment’
(http://www.ivir.nl/publications/other/DRM&levies-report.pdf)
(16 March 2005).
Hunen 2004
I. van Hunen, ‘Een nieuwe
gedaagde voor de muziekindustrie?’, JAVI, 2004 (6), 211-217.
Izal 2004
M. Izal and others, ‘Dissecting
BitTorrent: Five Months in a Torrent’s Livetime’,
(http://www.pam2004.org/papers/148.pdf), (28 March 2005).
Maslog-Levis 2005
K. Maslog-Levis, ‘BitTorrent
hubs close after ISP raid’ ZDNet Australia 18 March
2005
(http://www.zdnet.com.au/news/business/0,39023166,39185110,00.htm)(5
April 2005).
Mason 1997
A. Mason, ‘Developments in
the Law of Copyright and Public Access to Information’,
E.I.P.R. 1997, 19(11), 636-643).
Seignette 2001
J.M.B. Seignette, ‘Napster
en de controle van de rechthebbende over de distributie van zijn
werk’ AMI 2001(2), 29-34.
Skevik 2004
KA Skevik and others, ‘Analysis
of BitTorrent and its use for the Design of a P2P based Streaming
Protocol for a Hybrid CDN’,
(http://www.ifi.uio.no/dmms/papers/129.pdf), (28 March 2005).
Thompson 2005
C Thompson, ‘The BitTorrent
Effect’, Wired Magazine,
(http://www.wired.com/wired/archive/13.01/bittorrent.html), (28
March 2005).
Vanovermeire
2000
V. Vanovermeire, ‘The
Concept of the Lawful User in the Database Directive’,
I.I.C. 2000, 31(1), 63-81.
Vinje 1997
T.C. Vinje, ‘The New Wipo
Copyright Treaty: A Happy Result in Geneva’ E.I.P.R. 1997,
19(5), 230-236.
Visser 2001
D.J.G. Visser, ‘Napsteren,
Gnutellen en de Afwezigheid van Legale Muziek op Internet’,
Computerrecht 2001(3), 131-133.
Websites used
Cases referred to
The Netherlands
Rb. Haarlem, 12 May 2004, LJN
AO9318.
France
Cour D’Appel De Montpellier
3ème Chambre correctionnelle, 20 March 2005, Dossier
04/01534.
United Kingdom
Ladbroke (Football) Ltd v Hill
(William) (football) Ltd [1964] 1 WLR 274.
Electronic Techniques (Anglia)
Ltd v Critchley Components Ltd [1997] FSR 401.
Designers Guild Ltd v Russel
Williams (Textiles) Ltd [2000] 1 WLR 2416.
Newspaper Licensing Agency Ltd (NLA) v Marks & Spencer plc [2001] 3 WLR 290.
* Ribbert Van der Kroft Advocaten, Amsterdam, rietjens@rvdk.com.
1 Thompson 2005.
2 The Netherlands: Rb. Haarlem, 12 May 2004, LJN AO9318; France: Cour D’Appel De Montpellier 3ème Chambre correctionnelle, 20 March 2005, Dossier 04/01534.
3 Directive 2001/29/EC of the European Parliament and of the Council of 22 May 2001 on the harmonisation of certain aspects of copyright and related rights in the information society (“Infosoc Directive”); Directive 2000/31/EC of the European Parliament and of the Council of 8 June 2000 on certain legal aspects of information society services, in particular electronic commerce, in the Internal Market (“E–Commerce Directive”); Council Directive 91/250/EEC of 14 May 1991 on the legal protection of computer programs (“Software Directive”); and Directive 96/9/EC of the European Parliament and of the Council of 11 March 1996 on the legal protection of databases (“Database Directive”).
4 Berne Convention for the Protection of Literary and Artistic Works, 8th September 1886, completed at Paris (1896), revised at Berlin (1908), completed at Berne (1914), revised at Rome (1928), at Brussels (1948), at Stockholm (1967), revised at Paris 24th July 1971, amended 28th September 1979 (“Berne Convention”); WIPO Copyright Treaty, WIPO Doc. CRNR/DC/94, Dec. 20, 1996, 36 I.L.M. 65, art 10 (“WCT”); and WIPO Performances and Phonograms Treaty, Dec. 20, 1996, 36 I.L.M. 76 (“WPPT”). WCT and the WPPT shall collectively be referred to as: “WIPO Treaties 1996”.
5 This explanation is based on the following sources: Cohen 2003; Izal 2004; Skevik 2004; Thompson 2005; and www.wikipedia.com (search query: “BitTorrent”) (19 March 2005).
6 Berne Convention, art. 9.
7 Agreed Statements Concerning The WIPO Copyright Treaty, WIPO Document CRNR/DC/96, Agreed Statements Concerning Article 8, December 23, 1996.
8 WPPT, art. 7 and 11.
9 Infosoc Directive, art. 2.
10 Spoor 1996, 67.
11 Reed 2004, 11-15.
12 Lodder & Kaspersen 2002, 100.
13 Vinje 1997, 233; Mason 1997, 639.
14 Hugenholtz 2001; Arkenbout 2001.
15 UK Copyright, Design and Patents Act 1988, s. 16(3)(a). Compare: Ladbroke (Football) Ltd v Hill (William) (football) Ltd [1964] 1 WLR 274; Newspaper Licensing Agency Ltd (NLA) v Marks & Spencer plc [2001] 3 WLR 290; Designers Guild Ltd v Russel Williams (Textiles) Ltd [2000] 1 WLR 2416.
16 Stokes 2002, 42.
17 Electronic Techniques (Anglia) Ltd v Critchley Components Ltd [1997] FSR 401, para. 407-411.
18 Infosoc Directive, art. 2.
19 Reinbothe 2002, 86.
20 Infosoc Directive, recital 28.
21 Goldstein 2001, 268.
22 Berne Convention, arts. 11(1)(ii), 11bis(1)(i) and (ii), 11ter(1)(ii), 14(1)(ii) and 14bis(1).
23 Reinbothe 2002, 105.
24 Lodder & Kaspersen 2002, 101.
25 Fabiani 1997, 98; and Arkenbout 1997.
26 Lodder & Kaspersen 2002, 102.
27 Infosoc Directive, art 3.
28 WPPT, art. 10 and 14.
29 Infosoc Directive, art 3(2).
30 Hart 2002, 58-59.
31 WPPT, art. 15(1).
32 Cohen 2003, 2.
33 Reinbothe 2002, 105.
34 Lodder & Kaspersen 2002, 101.
35 Reinbothe 2002, 105.
36 Basic Proposal for the substantive Provisions of the Treaty on Certain Questions Concerning the Protection of Literary and Artistic Works to be Considered by the Diplomatic Conference, WIPO doc CRNR/DC/4 of 30 August 1996, note 10.14-10.16.
37 Hart 2002, 58
38 Reinbothe 2002, 112; Ginsburg 2004, 2.
39 Goldstein 2001, 262.
40 Copyinger 2005, para 7.98.
41 Reinbothe 2002, 112.
42 Reinbothe 2002, 107.
43 Infosoc Directive, art.2.
44 Lodder & Kaspersen 2002, 102.
45 Goldstein 2001, 293.
46 Visser 2000, 133.
47 Burrel & Coleman 2005, 302.
48 Dutch Copyright Act 1912, art. 16b et. seq.
49 UK Copyright, Design and Patents Act 1988.
50 Hugenholtz 2003, 46.
51 Alberdingk Thijm 2004, 51; Hunen 2004, 214; Visser 2001, 132; Bannink 2001, 28. Contra: Seignette, 2001, 32.
52 Rb. Haarlem, 12 May 2004, LJN AO9318
53 Cour D’Appel De Montpellier 3ème Chambre correctionnelle, 20 March 2005, Dossier 04/01534.
54 Dutch Copyright Act 1912, art. 16c.
55 Oxford Dictionary (search query: “private”)(http://www.oed.com)(30 March 2005)
56 Ibid.
57 Hugenholtz 2003, 10-12.
58 Hart 2002, 59.
59 Infosoc Directive, art. 5(1).
60 Reed 2004, 11-15.
61 Vanovermeire 2000, 63.
62 This interpretation seems to be adopted with regard to the use of computer programs in the United Kingdom. CDPA, art. 50A(2): “For the purposes of this section and sections 50B, 50BA and 50C a person is a lawful user of a computer program if (whether under a licence to do any acts restricted by the copyright in the program or otherwise), he has a right to use the program.”
63 E-Commerce Directive, art 12.
64 E-Commerce Directive, art 12(1).; and Directive 98/48/EC of the European Parliament and of the Council of 20 July 1998 amending Directive 98/34/EC laying down a procedure for the provision of information in the field of technical standards and regulations, art. 1(2).
65 E-Commerce Directive, art 12(2).
66 E-Commerce Directive, art. 12(1)(b).
67 Maslog-Levis 2005.
68 See for example p2p program named “Exeem” (http://www.exeem.com)(7 April 2005).
69 Ginsburg 2004, 12.


