| Topic |
Paragraphs |
| Introduction |
1-2 |
| The witnesses |
3-11 |
| Prof Marshall |
3-7 |
| Dr Brydon |
8-11 |
| The skilled person |
12 |
| Common general knowledge |
13-65 |
| UMTS |
15-16 |
| Basic network infrastructure in UMTS |
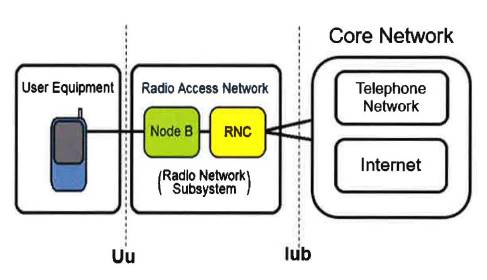
17-18 |
| CDMA |
19-20 |
| Duplexing |
21 |
| Layers, protocols and stacks |
22-26 |
| Transmission Time Interval |
27-30 |
| HSDPA |
31-32 |
| HSUPA |
33-35 |
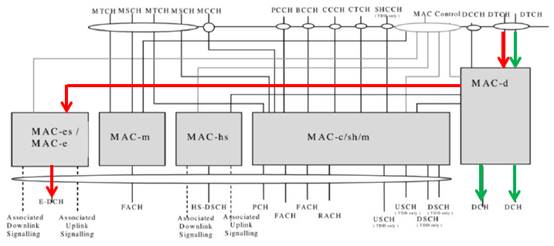
| E-DCH architecture |
36-39 |
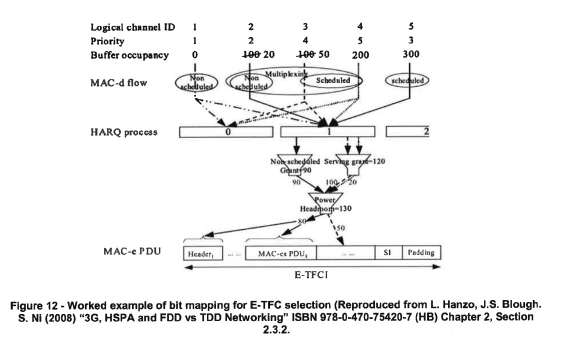
| E-TFCs |
40 |
| Rise over Thermal |
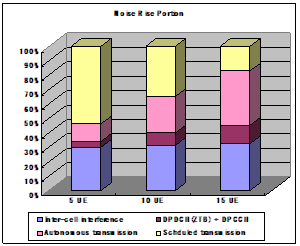
41-44 |
| Scheduled and non-scheduled grants |
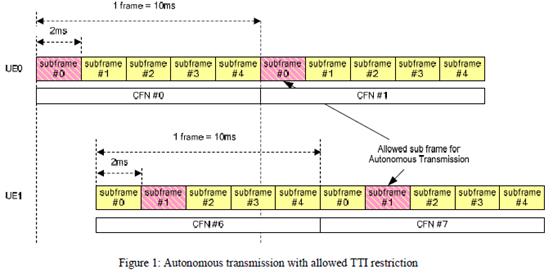
45-50 |
| The power headroom |
51 |
| The minimum set |
52-53 |
| HARQ |
54-61 |
| E-TFC selection and E-DCH transmissions |
62-65 |
| The Patent |
66-147 |
| Field of the invention |
67-68 |
| Description of the related art |
69-75 |
| Summary of the invention |
76-90 |
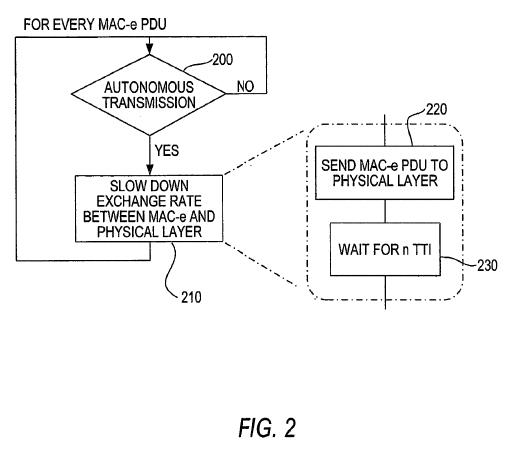
| Detailed description of the presently preferred embodiments |
91-147 |
| The claims |
148-150 |
| Construction |
151-167 |
| [A] A method
for autonomous uplink transmission |
152-155 |
| [B] a virtual transmission time interval for a medium access control entity |
156-159 |
| [B] which virtual transmission time interval defines a minimum time interval that is allowed between enhanced uplink transmissions |
160 |
| [C] data packets |
161 |
| [C] checking to determine whether the medium access control entity is transmitting data packets in a current air interface transmission time interval, by checking whether the medium access control entity is able to empty the radio link control buffer in the current air interface transmission time interval |
162-167 |
| Essentiality |
168-205 |
| Uplink DTX |
168-169 |
| Uplink DRX |
170-179 |
| Buffer Occupancy |
180-184 |
| Retransmissions in Uplink DRX |
185-190 |
| Conversant's case in outline |
191-194 |
| Integer A |
191 |
| Integer B |
192 |
| Integer C and D |
193-194 |
| Assessment |
195-205 |
| Integer A |
195 |
| Integer B |
196 |
| Integer C |
197-205 |
| Added matter |
206-227 |
| The law |
206 |
| Assessment |
207-209 |
| Allegation 1 |
210-213 |
| Allegation 2 |
214-215 |
| Allegation 3 |
217-218 |
| Allegation 4 |
219-226 |
| Allegation 5 |
227 |
| Obviousness |
228-258 |
| Samsung |
229-244 |
| The disclosure |
229-234 |
| Obviousness |
235-245 |
| Terry |
246-258 |
| The disclosure |
246-25 |
| Obviousness |
256-258 |
| Insufficiency |
259 |
| Summary of principal conclusions |
260 |